A common programming mistake is thinking that what can’t be seen on the public web can’t possibly be a vulnerability. WordPress site owners entrust their security to plugin developers, which isn’t a great idea. Usually, site owners find out that a plugin has a vulnerability after it’s already been exploited. This is the case for a WordPress hook function in the King addon for Elementor.
Elementor is a popular plugin itself, but the King addons extended some of its functions like adding widgets, templates and AI tools. The developer claims that the King addons have over one million installations spanning the developer’s own site, Envato and WordPress downloads. Because of the severity of the vulnerability and the number of installs, CVE-2025-8489 has a critical severity label. Critical severities should be taken seriously by anyone with the plugin installed, so update to at least version 51.1.37 immediately.
WordPress Plugin Vulnerability Explanation
Although the vulnerability in the Elementor King addon is critical, the exploit is quite simple. You don’t need cookies or authentication, which is why it’s such a dangerous issue. Before explaining the vulnerability, let’s go through what Elementor and the King addon does for a WordPress site.
Elementor is an addon that helps site owners create pages. It has thousands of templates and widgets to make page creation and website design easier, especially if you aren’t a designer or coder. With convenience, security is often compromised, and this is what happened with the addon.
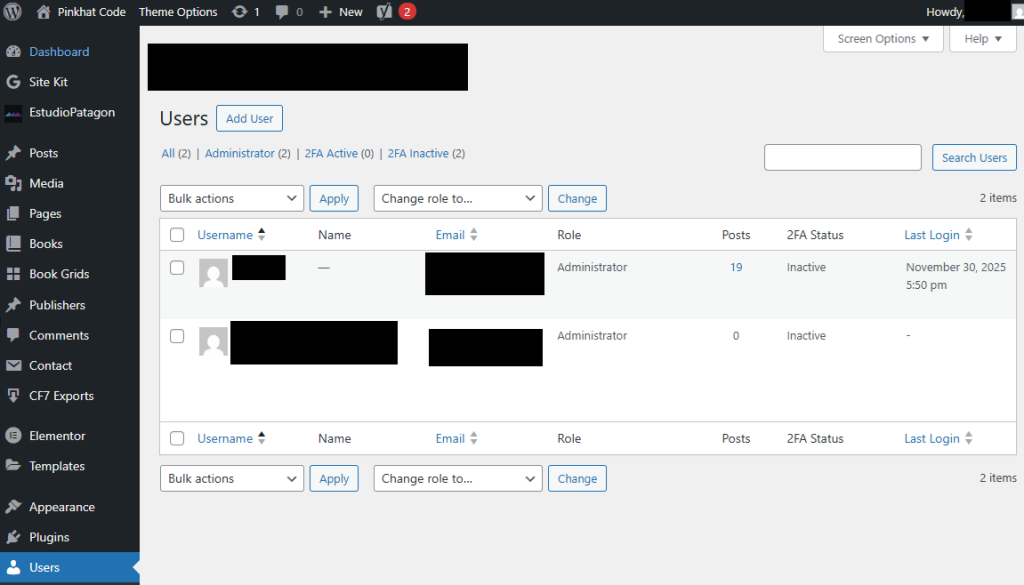
WordPress has an Ajax handler for creating new users. When you go into your WordPress dashboard, you see all the new users created. An administrator account is automatically created when you install WordPress, but the admin can also add additional admin users:
Plugins have access to the WordPress “create_user” handler, but the King addon has its own function. When you have a form created from a King addon template, you can have the form create a new user. Usually, the intention is to create a new user with the subscriber role. Users with the subscriber role can make comments and get updates, but they can’t do any administrative actions to the site.
Because input is user generated, the input should be validated. This type of user-generated input is often overlooked because it’s the system making a call to the WordPress hook, but (as you will see in the proof of concept) a call to the handler can be direct. The King addons developers failed to validate user input and failed to limit the type of user that can be created by the backend function. This leads to an attacker creating an administrator user, which has total control over the WordPress site.
No notification is sent to the site owner, so an attacker can silently make any number of changes to the site including content injection, data eavesdropping malware, malware downloads, phishing, or simple site destruction like defacing the site or deleting content.
Proof of Concept for CVE-2025-8489
No special coding or configuration is needed to exploit the King addon vulnerability. The vulnerability is located in the function “king_addons_user_register”. You can even do it for free from a website that offers HTTP requests via a web application. A good example is ReqBin. You can send HTTP POST requests from this site. To perform the exploit, you need a site with Elementor and King addons. If you are unsure if your site has this vulnerability, you can perform these steps to test it.
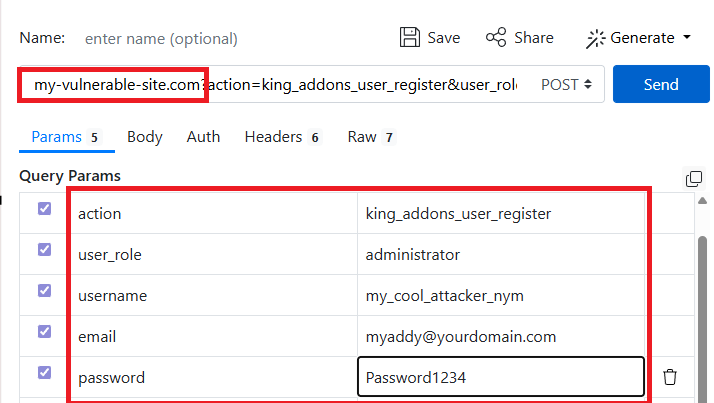
First, go to ReqBin (or any other HTTP request application like Burp Suite). Fill out the form:
You only need to fill out the vulnerable domain and then fill out the query parameters. The site will add the query string parameters to the URL. Make sure that you have POST selected in the URL input box.
Click “Send” when you are done. If your site is vulnerable, you should see a new user in your WordPress dashboard with the name “my_cool_attacker_nym” with administrator privileges.
What to Do If Your Site Is Vulnerable
The first thing to do is download the latest version of King Addons for Elementor. If you pay for premium, you might need to download the patch from the developer site or via your WordPress dashboard. The patch forces a new user request to only allow subscribers, making malicious registration requests ineffective.
For developers, always validate input even if you think only the system will make the call. If the call to a function can be made from a third party, you must validate input. Reject any user-generated input that does not follow a set standard that you set for the application. Always default permissions to the lowest privilege level, in this case a subscriber on WordPress.