Ecommerce fraud is a favorite for hackers all year, but Christmas time is especially popular for account takeover and credential stuffing. Account takeover (ATO) happens when an attacker has a list of usernames and passwords and uses automation software to attempt authentication across sites. The attack itself is called credential stuffing, and the result is compromised accounts. Usually, a successful authentication means that the attacker has access to other sites, because ecommerce customers notoriously use the same passwords across multiple sites.
You would think that once an attacker has a positive authentication hit that they would use the vulnerable user’s account to purchase items, but you would be wrong. It’s popular for attackers to verify that multiple accounts are vulnerable and then sell a list of them on darknet markets. Consumers can’t do much about vulnerable ecommerce sites that allow automated authentication attempts. Most consumers are unaware of security standards and the need for different passwords across sites. As an ecommerce site owner, you can provide some protection to your customers and your brand reputation by preventing account takeover attacks.
This article helps small ecommerce businesses understand fraud protection and what you can do to stop account takeover fraud without spending big bucks on expensive fraud detection software. Some of it is technical and some of my content is more generalized for ecommerce site owners who just want information about common hacks targeting their websites. ATOs are especially dangerous for ecommerce because you don’t need much technical prowess to get a list of vulnerable user accounts.
How Attackers Perform ATO with Credential Stuffing Tools
The first step for an attacker is to get a list of raw credentials. These credentials are usually sold on dark web onion sites or clearnet forums like Breach Forums or Raid Forums (both now defunct for illegal activities). Although gone, the people running the site are still around, mostly on DarkForums. There was talk of them returning to the clearnet with the breach-forums.st domain, but it’s still down.
If you want to be a particularly proactive ecommerce store owner, you can subscribe to services like Dehashed.com. Dehashed gives you a heads-up if your customers’ information was found on the web, but you should know if your site has been breached before customer data is published. Fraud detection software will send alerts if it detects anomalies on your site.
If you, as an individual, want to know if your email has been included in a breach, you can visit HaveIBeenPwned.com. It will tell you all the data breaches that contain your email address.

Image of my email pwnd results
Now, how does an attacker take that list and use your ecommerce site for account compromise validation? Attackers can write their own Python scripts or use downloaded software. The latter makes ATO especially dangerous for consumers and ecommerce sites because no coding experience is required to perform the attack.
If you’re curious, here are a few credential stuffing applications that let attackers load a list and simply click “Run” to perform ATO. All of them support proxies, so blocking attacks using IP addresses is not effective.
Sentry MBA
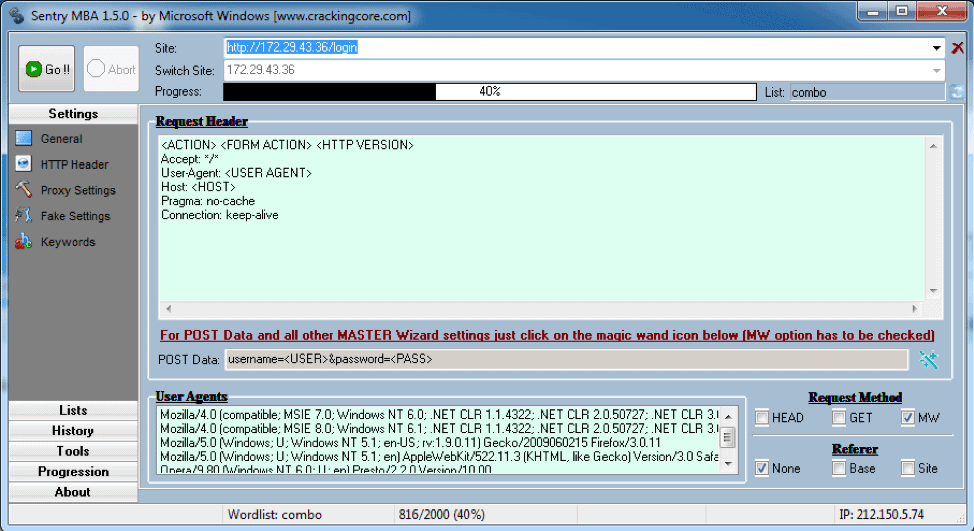
Sentry MBA interface
As you can see, an attacker loads a list of credentials, points Sentry MBA to your login page, and clicks “Go” to let the software run. Any hits will display in the window, and this tells the attacker which credentials from the list are valid.
OpenBullet
OpenBullet interface
Just like Sentry MBA, OpenBullet takes a credential list and shows attackers which authentication request was successful.
SNIPR
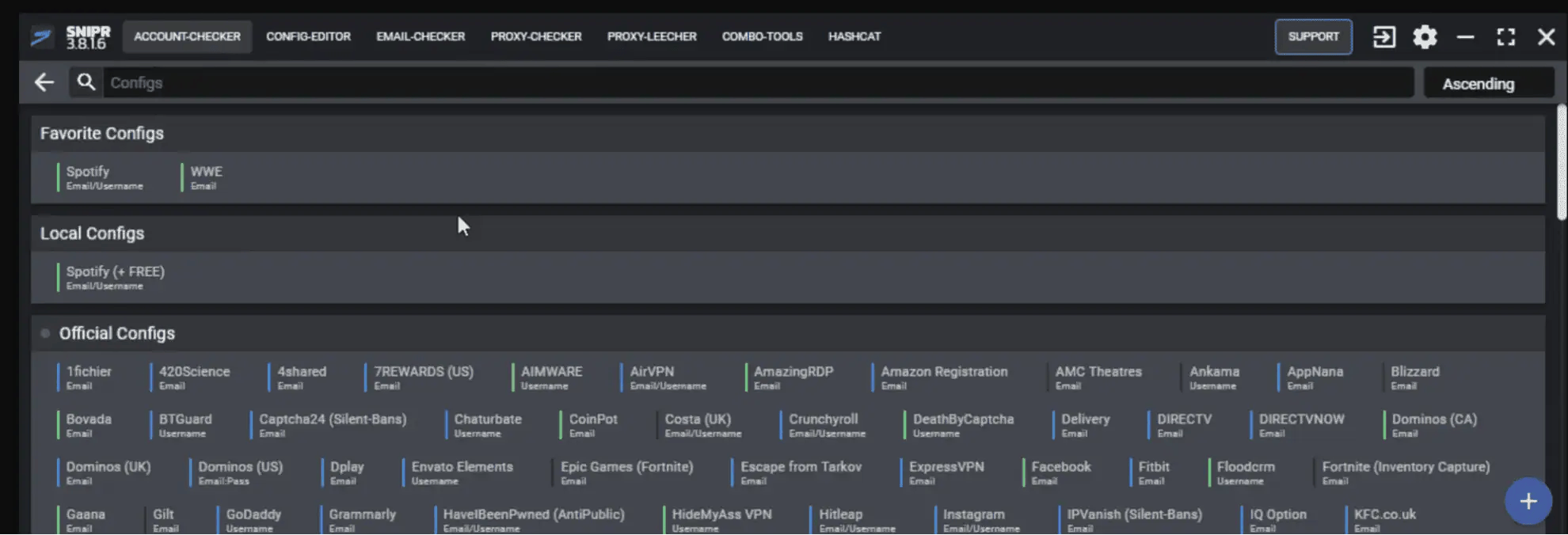
SNIPR interface
SNIPR is much more advanced than previous password checkers. You can configure it out-of-the-box to compromise specific websites. In this image, the attacker is aiming for Spotify accounts.
I know this doesn’t sound technical at all, but this is all it takes for an attacker to compromise your ecommerce site and steal your customer data. As a small site owner, you can only imagine how devastating a successful breach can be on your reputation. As an example, the ecommerce site Kiddicare went out of business in 2019 after attackers stole data from their test site. Numerous others small enough to be anonymous have also gone out of business simply from litigation and damaged brand reputation.
What You Can Do: Ecommerce Fraud Prevention with Credential Stuffing Protection
Numerous cybersecurity businesses offer fraud protection and detection. Every one has its own pros and cons, but this article is meant to help small ecommerce businesses protect themselves from ATO without spending a lot of money. Many of the big fraud prevention applications are expensive, but you can perform a few small additions to your site’s authentication workflow to stop ATO without spending big bucks.
Add a CAPTCHA to the Login Form
Whether you have a platform like WordPress or Square or you have a customized site, you can add a CAPTCHA to your login form. Some store owners choose to show a CAPTCHA only after a few login attempts. This stops some credential stuffing attacks, but it doesn’t stop them if the attacker has accurate credentials for a user and can authenticate on the first attempt. CAPTCHA on an authentication form stops automatic attacks instantly so bots won’t be able to submit the form at all, also saving your server resources from multiple attempts.
Use CloudFlare
CloudFlare can’t stop a bot from submitting an authentication request, but it can detect bots and strange behavior. If an attacker’s software hits the server too quickly, CloudFlare will block it as a bot or a simple denial-of-service attempt. CloudFlare has several other benefits like hiding your server’s IP so that it cannot be taken down by a distributed denial of service (DDoS). You can use a free version to test it out.
Lock Accounts after a Few Failed Authentication Attempts
Authentication locking will require your programmer or a plugin if you use something like WordPress. Don’t make the number of attempts too little, or you could lock out legitimate users who forgot their passwords. It’s reasonable to lock an account for a few minutes after 4-5 login attempts. You can alert users or have them reset their passwords.
These three low cost changes will greatly reduce your risk of being a victim of a data breach from credential stuffing and account takeover attacks. It won’t stop all attacks on your ecommerce store, but it’s one step in the right direction for protecting your customers.

