They say that we should only install software from a known trusted developer, but what happens when that trusted developer goes rogue? Cybersecurity researchers recently found that a popular Chrome extension named Urban VPN Proxy with a 4.7 star rating and over six million installations has malicious code meant to eavesdrop data, specifically eavesdrop on AI prompts typed into your browser meant for AI chatbots. Researchers found that Urban VPN Proxy intercepts prompts typed into Gemini, Claude, ChatGPT, Perplexity, and Grok.
Data Harvesting from AI Prompts is the New Data Eavesdropping
Proxy and Virtual Private Network (VPN) services are always marketed as a way to protect your data from eavesdropping. In case you don’t already know, a VPN “tunnels” data so that it can’t be intercepted and eavesdropped by a third party on the network. VPNs are used in an enterprise to protect users connected to public Wi-Fi networks.
Urban VPN Proxy has millions of downloads
Implicit trust is a common problem for users installing third-party extensions. While Urban VPN Proxy users thought they were hiding their data, they were actually exposing anything they typed into AI chatbots to malicious developers. Any users on a work computer could also expose enterprise secrets or intellectual property.
As of this writing, the Chrome extension (also available on the Edge marketplace) is still available for download. The Chrome extension code is not publicly available without downloading the source code, but researchers at Koi posted the malicious code where the application is programmed to listen into AI prompts.
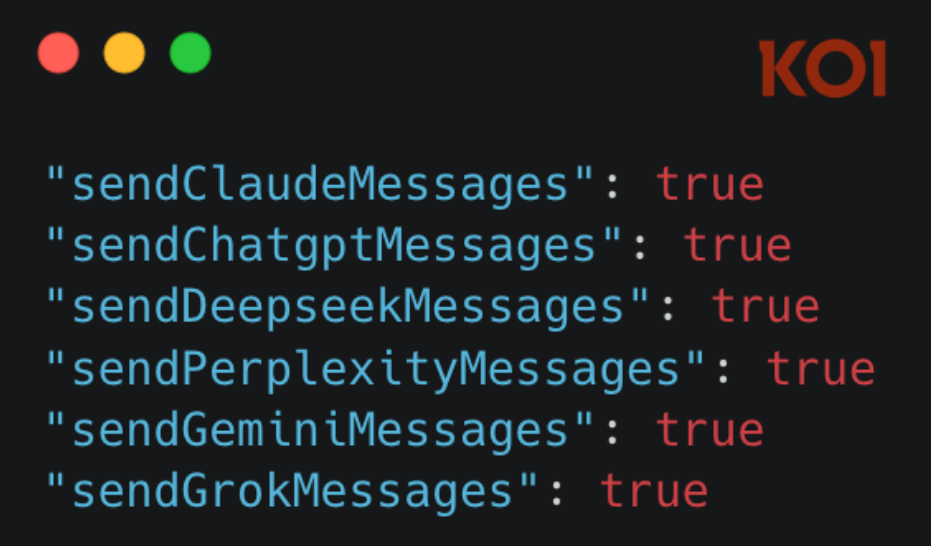
Koi researchers found the browser extension malicious code
Nothing strange happens from the front end, so users are unaware that Urban VPN Proxy is listening to the information sent to AI APIs. The code is a wrapper that intercepts what users type into their browser to get AI-generated answers. Urban VPN Proxy intercepts the prompt, exfiltrates the data, and then sends the AI prompt to the model’s API, so users get answers as if nothing happened. To the user, the Chrome extension works normally.
Data exfiltration and eavesdropping weren’t introduced to the extension until July 2025, so users were safe until this point. If you have Urban VPN Proxy version 5.5.0 installed, you are currently sending data to third-party developers and ad agencies. You can remove the extension, and no known update reverses this change. At the same time that the new version added the data harvesting feature, Urban VPN Proxy also updated its ToS to say that the company collects user data. It’s a lesson to always read company ToS changes to understand if they collect your private information.
Data Exfiltration to the Malicious VPN Endpoint
Unless you have network traffic analysis running on your network, you wouldn’t notice the extra traffic sent to endpoints. Urban VPN Proxy sends the eavesdropped AI prompt messages to their endpoints on analytics.urban-vpn.com and stats.urban-vpn.com.
All the major browsers have features to handle requests sent to third-party APIs or external sources without refreshing the page. Installed browser extensions can override these features. Anything installed on a browser has access to many features that you wouldn’t want to give without trusting the developer.
The Urban VPN Proxy code overwrites fetch() and XMLHttpRequest() features for all the big browsers. Browsers use these two functions to call AI chatbots APIs and return answers to users. AI chatbots use JavaScript files to bridge communication between the AI LLM and users, so calls to files such as chatgpt.js, claude.js, gemini.js are intercepted first before sending the query to the AI API.
It appears that the data is harvested and sent to an ad intelligence corporation named BIScience. Ad agencies use this data to give you more targeted ads, but having access to raw data also exposes you to data theft, identity theft, and general data misuse. The same developer for Urban VPN Proxy also injected the same data harvesting code into two other extensions: 1ClickVPNProxy and Urban Ad Blocker.
What Can You Do to Remove the Data Eavesdropping?
The developers for Urban VPN Proxy seem to be collecting data purposely and added changes to their ToS, so it’s likely that there will not be a reversal of these changes. The only way to stop the data harvesting and sending data to ad analytics agencies is to remove the extension from your browser.

